Cybersecurity Frameworks
This section will cover different frameworks in cybersecurity.
Table of Contents
- Introduction
- Pyramid of Pain
- TTPs - Tough
- Tools - Challenging
- Network/Host Artifacts - Annoying
- Domain Names - Simple
- IP Addresses - Easy
- Hash Values - Trivial
- Cyber Kill Chain
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control (C2)
- Action on Objectives
- Unified Kill Chain
- Phase: In - Initial Foothold
- Reconnaissance
- Resource Development
- Delivery
- Social Engineering
- Exploitation
- Persistence
- Defence Evasion
- Command and Control
- Phase: Through - Network Propagation
- Pivoting
- Discovery
- Privilege Escalation
- Credential Access
- Lateral Movement
- Phase: Out - Action on Objectives
- Collection
- Exfiltration
- Impact
- Objectives
- Phase: In - Initial Foothold
- Diamond Model of Intrusion Analysis
- Adversary
- Victim
- Capability
- Infrastructure
- Event Meta-Features
- MITRE
Introduction
Cybersecurity frameworks such as the Pyramid of Pain, MITRE, and the Diamond Model can help us understand the different stages of an attack, helping us breakdown what an attacker will do and the steps we can take to stop them.
Pyramid of Pain
The Pyramid of Pain is a hierarchy of indicators that can support us in detecting adversaries. It showcases the difficulty of collecting different types of indicators and the impact when gathering intelligence for them.
The pyramid consists of 6 indicators:
- TTPs - Tough
- Tools - Challenging
- Network/Host Artifacts - Annoying
- Domain Names - Simple
- IP Addresses - Easy
- Hash Values - Trivial
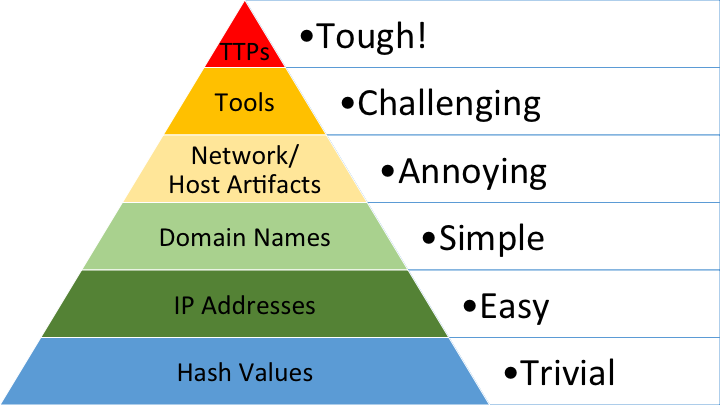
As we ascent the pyramid, obtaining the Indicators of Compromise (IOCs) becomes increasing challenging. However, this also means that the adversaries will need to alter their attack methodologies, which can be hard depending on the stage.
TTPs - Tough
Tactics, Techniques, and Procedures (TTPs) refers to all the steps taken by an adversary to achieve their goal.
If we are able to detect and respond to TTPs, an attacker would need to reconfigure their tools, potentially find and build new ones, use different attack vectors, and more.
An example will be where we are able to detect a pass-the-hash attack by monitoring Windows Event Log and remediate it. This allows us to find the compromised host and stop any lateral movement within the network.
We can use the MITRE ATT&CK matrix to help map the TTPs that an attacker would use.
https://attack.mitre.org/
Tools - Challenging
If we are able to detect the tools used by the attacker, it can be challenging for them to change their tools as they would need to create a new tool for the same purpose or learn a new tool.
We can use antivirus signatures, detection rules, YARA rules, and more to detect the tools used by an attacker. We can obtain samples and signatures from sites such as MalwareBazaar and Malshare that can then be used to create rules to hunt for the attacker.
MalwareBazaar - https://bazaar.abuse.ch/
Malshare - https://malshare.com/
Network/Host Artifacts - Annoying
At this level, it will be annoying for the attacker if we are able to detect their attacks as they would need to potentially change their attack tools and methodologies, which can be a time consuming process.
Network artifacts are unusual or suspicious network activity such as inbound/outbound connections to the host, Command and Control (C2) information and communication, specific URI patterns, user-agent strings, and more.
We can use tools such as Wireshark or monitor network logs for unusual or suspicious behaviour.
Host artifacts are traces or observables that an attacker leaves on the system such as registry values, suspicious process execution, attack patterns, IOCs, files, and more.
We can use tools such as Sysmon and Event Viewer on Windows to look for suspicious or potential malicious activity such as unusual process behaviour.
An example of such artifacts that would indicate a compromise will be where an attacker is able to download a malicious file onto a system that is then communicating back to a C2 server to exfiltrate sensitive information.
Domain Names - Simple
Domain names are used to map IP addresses to hostname (domain name). This allows the user to remember a human-friendly name such as gohspace.com instead of an IP address such as 192.168.222.113.
If we are able to detect and block malicious domains, it can be a pain for the attacker to change the domain as they will need to purchase a new domain, register it, and modify the DNS records.
Attackers can also use Punycode to pretend to look like a legitimate domain. Punycode is a way of converting words that cannot be written in ASCII, into a Unicode ASCII encoding. This is known as a Punycode attack.
Attackers can also use URL shorteners to create a short and unique URL that will redirect to their malicious domains. To view the website that the link shortener is redirecting to, we can append the plus (+) character at the end of the URL.
IP Addresses - Easy
An IP address is used to identify any device connected to a network. These devices can range from computers, cameras, smart devices, IOT devices, servers, and more.
Obtaining the attacker IP addresses can be crucial as this can allow us to block, drop, or deny inbound and/or outbound network requests on the firewall or perimeter to the malicious IP addresses.
When analysing malware, we can use tools such as AnyRun to gather information on network connections or monitor network traffic logs.
Hash Values - Trivial
Hashes are one way, non-reversible mathematical functions. It allows us to obtain a fixed length value that uniquely identifies data. These values are the result of a hashing algorithm.
The following are some common hash algorithms:
- MD5
- SHA-1
- SHA-2
A hash is not considered to be cryptographically secure if two different files can have the same hash value or digest. This is called a hash collision.
Hash values can be used to gain insight into a specific piece of file, such as a malicious or suspicious file as it allows us to uniquely identify and reference the malicious artifact.
These hash values can be passed to tools such as VirusTotal to perform a hash lookup to see if the file has been analysed.
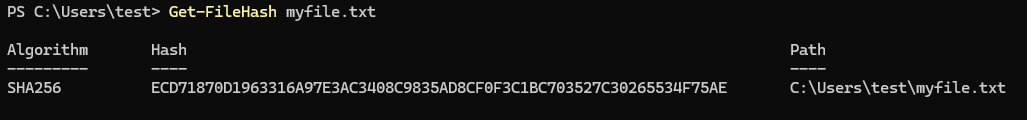
To obtain the file hash, we can use Get-FileHash in Windows or <hash>sum in Linux (i.e. sha256sum).
On Windows:
Get-FileHash myfile.txt
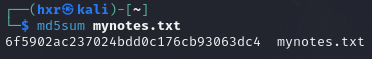
On Linux:
md5sum mynotes.txt
Due to the uniqueness of a hash value, when a file is modified even by a single character, it can change the entire hash value. This means that we should not solely rely on the hash value of files to detect malicious activity.
Cyber Kill Chain
The Cyber Kill Chain developed by Lockheed Martin, is one of many attack life cycles and frameworks.
The Cyber Kill Chain consists of 7 stages:
- Reconnaissance
- Weaponization
- Delivery
- Exploitation
- Installation
- Command and Control
- Action on Objectives
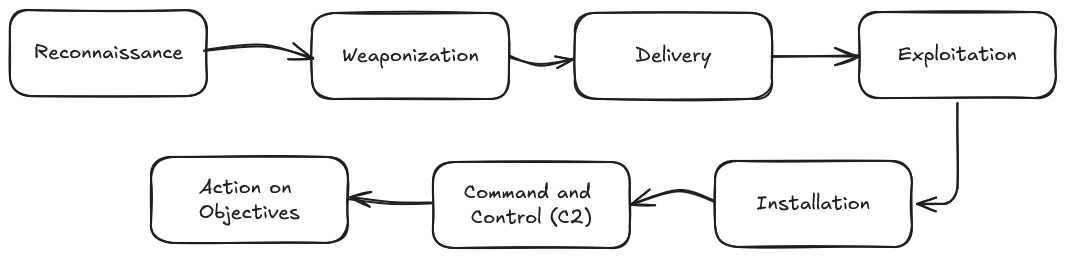
By understanding the kill chain, it allows us to better respond and understand cybersecurity incidents and the attacker's objectives.
Reconnaissance
The reconnaissance stage is where information gathering happens. At this stage, information on the target such as system or user information are collected that can then be used to perform attacks.
Some ways that an attacker can gather information are using Open Source Intelligence (OSINT), performing port scans, and more.
OSINT is where an attacker uses publicly available resources such as viewing the target's website and visiting the employees social media accounts.
The following are some tools that can be used to gather information:
theHarvester - https://github.com/laramies/theHarvester
Hunter - https://hunter.io/
OSINT Framework - https://osintframework.com/
An example of recon will be where an attacker visits the employees social media pages to gather more information on their positions and activities to perform phishing attacks.
Weaponization
The weaponization stage is where the attacker creates the malware that will be used to gain initial access using the information collected during the reconnaissance stage.
To create the payload that will be used to gain access, the attacker would combine malware and a exploit into a deliverable payload. There are many ways to do this such as creating your own or using readily available malware.
The following are some definitions for this stage:
| Term | Description |
|---|---|
| Malware | Stands for Malicious Software. It is a program or software that has been designed to damage, disrupt, or gain unauthorised access to a system. |
| Exploit | A exploit is a method or code that takes advantage of a vulnerability in the system. |
| Payload | A payload is a piece of malicious code that the attacker can use to cause harm to the target. |
An example will be where an attacker creates a Microsoft Word document that contains a malicious macro that runs when the victim opens it.
Delivery
The delivery stage is where the malware/payload created in the previous stage is sent to the target.
Some ways the malware/payload can be delivered are via phishing emails, pretending to be a legitimate site, compromising a known website that the target visit often (watering hole attack), and so on.
An example will be where it is sent via phishing where a malicious attachment is sent or sending a URL that mimics another website to trick the user into entering their credentials.
Exploitation
The exploitation stage is where the initial stager is executed and is running on the target system. During this stage, the attacker typically attempts to execute code on the target system to gain deeper access or more control.
Once an attacker gains access via the malware they sent, they can move laterally, gaining access to more systems or vertically, gaining higher privileges. This is done to gain more access or control.
Some examples of how an attacker can exploit are:
- Phishing (i.e., opening a malicious attachment or click on a malicious link)
- Using a zero-day exploit
- Exploiting vulnerabilities on hardware or software
There are many different ways that an attacker can use to gain initial access and gain more deeper access to their target.
Installation
The installation stage is where the attacker attempts to establish persistence. This allows them to return to the system if the initial access point has been patched or if they lose connection to the network.
This is also the stage where attackers install additional malware to gain further access to the system.
The following are some methods an attacker can use to achieve persistence:
- Creating a web shell
- Installing a backdoor
- Modifying services
- Modifying the Windows registry or adding auto-run jobs of malicious programs
An example will be where an attacker has compromised the system and creates a web shell on the victim's website, allowing the attacker to maintain access to the system and potentially execute commands.
Another technique an attacker can use at this stage is Timestomping. This is a technique that allows the attacker to avoid detection by a forensics investigator by modifying the malicious file timestamps such as modify, access, create, and change the time.
Command and Control (C2)
The Command and Control (C2) is where communications happen between the C2 server and malware on the affected hosts. This allows the compromised hosts to consistently communicate with the C2 server (attacker).
Other terms for this stage are:
- C2 Beaconing
- C&C
If an attacker is able to establish a C2 communications, it usually means they have achieved full system control.
Attackers can use standard ports such as 443 (HTTPS) or 80 (HTTP) to masquerade as legitimate traffic, making it harder to perform incident response.
Other C2 channels includes using DNS to make constant requests to the DNS server that belongs to the attacker. This is also known has DNS Tunnelling.
Action on Objectives
The Action on Objectives stage is where the attacker achieve their goals. Depending on their goals, the methods used can be different.
Some common goals are:
- Collect more information from users
- Perform privilege escalation to gain more access
- Perform more reconnaissance
- Deleting backups
- Overwrite or corrupt data
- Monetary gains (i.e., ransomware)
An example will be where an attacker managed to gain full system control by performing the previous stages and exfiltrated data using the C2 channel created in the previous stage.
Unified Kill Chain
Understanding the behaviours, objectives, and methodologies of cyber threats can help establish a strong cybersecurity posture (defence).
The purpose of the Unified Kill Chain (UKC) is to complement and not compete with other cybersecurity kill chain frameworks such as the Cyber Kill Chain by Lockheed Martin and MITRE's ATT&CK.
There are 18 phases to an attack in the Unified Kill Chain:
- Reconnaissance
- Resource Development
- Delivery
- Social Engineering
- Exploitation
- Persistence
- Defence Evasion
- Command and Control
- Pivoting
- Discovery
- Privilege Escalation
- Execution
- Credential Access
- Lateral Movement
- Collection
- Exfiltration
- Impact
- Objectives
These phases can be grouped into a few areas:
- Phase: In - Initial Foothold
- Phase: Through - Network Propagation
- Phase: Out - Action on Objectives
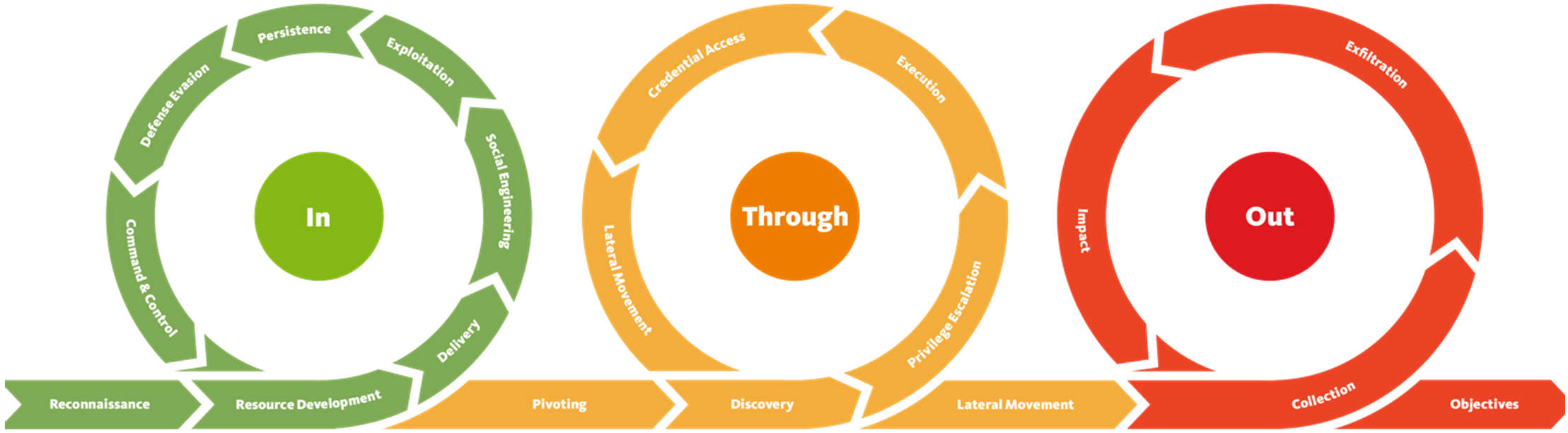
Some benefits of using the UKC is that it is modern (released in 2017, last updated in 2023 as of writing this), it is detailed when compared to other frameworks, it covers an entire attack, and has a much more realistic scenario.
Visit the White Paper on the Unified Kill Chain for more information:
https://www.unifiedkillchain.com/assets/The-Unified-Kill-Chain.pdf
Phase: In - Initial Foothold
This series of phases focuses on gaining initial access and creating persistence on the target.
The following phases are:
- Reconnaissance
- Resource Development
- Delivery
- Social Engineering
- Exploitation
- Persistence
- Defence Evasion
- Command and Control
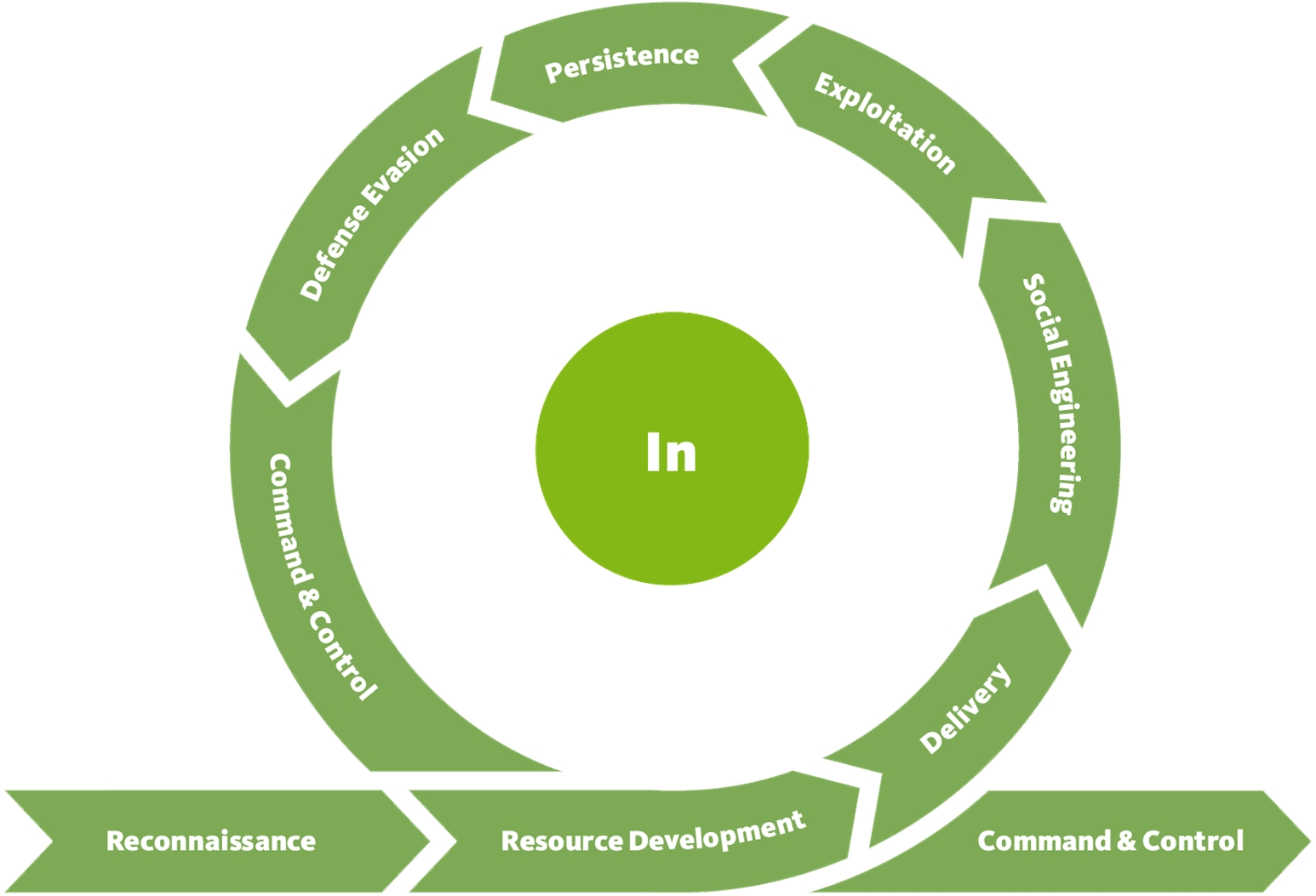
The phases here will be linked to MITRE ATT&CK tactics as examples.
Reconnaissance
This phase describes the techniques used by an adversary to gather information relating to their target. This can be done through many different ways such as passive or active recon.
Some information that can be gathered at this phase are:
- System information (i.e., host operating system, IP address, etc.)
- List of employees and their information such as email addresses
- Potential credentials that can be used. Some sources can be previous data breaches
- Network topology and configuration
- Defences being used and configuration
This phase can be linked to "Reconnaissance" (TA0043) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0043/
Resource Development
This phase describes the adversary setting up the necessary infrastructure, creating or purchasing the tools, malware, and other capabilities that are required for the attack.
An example will be where an attacker is creating a payload that can then be used to gain initial access to the target systems.
This phase can be linked to "Resource Development" (TA0042) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0042/
Delivery
This phase describes the adversary using various methods to get items such as the payload from the resource development phase onto the target to gain initial access.
An example will be where an attacker is able to upload a web shell onto the target web server and execute commands on the system.
This phase can be linked to "Initial Access" (TA0001) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0001/
Social Engineering
This phase is a technique that an adversary can use during their attacks. Social engineering is an attack where the victim is manipulated or tricked to perform certain actions such as opening a malicious word document.
Some types of social engineering attacks are but not limited to:
- Phishing
- SMS phishing (smishing)
- Spear phishing
- Voice phishing (vishing)
- tailgating
- Quid pro quo
- Baiting
- Pretexting
An example of a phishing social engineering attack will be where the attacker sends the victim a email disguised as a legitimate email to trick them into clicking a URL.
This phase can be linked to "Phishing" (T1566) in the MITRE ATT&CK framework:
https://attack.mitre.org/techniques/T1566/
Additional resources:
- https://www.ibm.com/topics/social-engineering
- https://www.cisco.com/c/en/us/products/security/what-is-social-engineering.html
Exploitation
This phase describes how an adversary takes advantages of vulnerabilities present in a system. The UKC defines "Exploitation" as abuse of vulnerabilities to perform code execution.
Some examples are:
- Uploading and executing a reverse shell on a web application
- Interfering with an automated script on the system to execute code
- Abusing vulnerabilities on a web app to execute code on the system that it is running on.
An example will be where an attacker is able to upload and run a web shell via a file upload function due to improper input sanitation and validation.
This phase can be linked to "Execution" (TA0002) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0002/
Persistence
This phase describes the techniques used by an adversary to maintain access to a compromised system that they have access to.
Some examples are:
- Creating a service on the target system that allows the attacker to regain access
- Creating a user account that the attacker has access to on the target system
- Installing backdoors and executing them when a certain action is performed on the target system
An example will be where the attacker creates a script that allows them to connect to the target system and is ran each time the target system is restarted by creating a Task Scheduler task in Windows.
This phase can be linked to "Persistence" (TA0003) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0003/
Defence Evasion
This phase describes the techniques used by an adversary to evade defensive measures placed in the network or system.
Some examples of defensive measures are:
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Firewalls
- Web Application Firewalls
- Anti-virus/Anti-malware
An example will be where an attacker writes a custom malware to avoid being detected by antivirus solutions.
This phase can be linked to "Defense Evasion" (TA0005) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0005/
Command and Control
This phase describes how an adversary is able to establish communications with themselves (their own servers) and the target system.
There are many different techniques attackers can use to setup and establish a connection to avoid getting caught.
With Command and Control (C2) communications, adversaries can perform actions such as exfiltrating data or running commands.
This phase can be linked to "Command and Control" in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0011/
Phase: Through - Network Propagation
This series of phases focuses on gaining additional access and privileges to the systems, network, and data.
The following phases are: 9. Pivoting 10. Discovery 11. Privilege Escalation 12. Execution 13. Credential Access 14. Lateral Movement
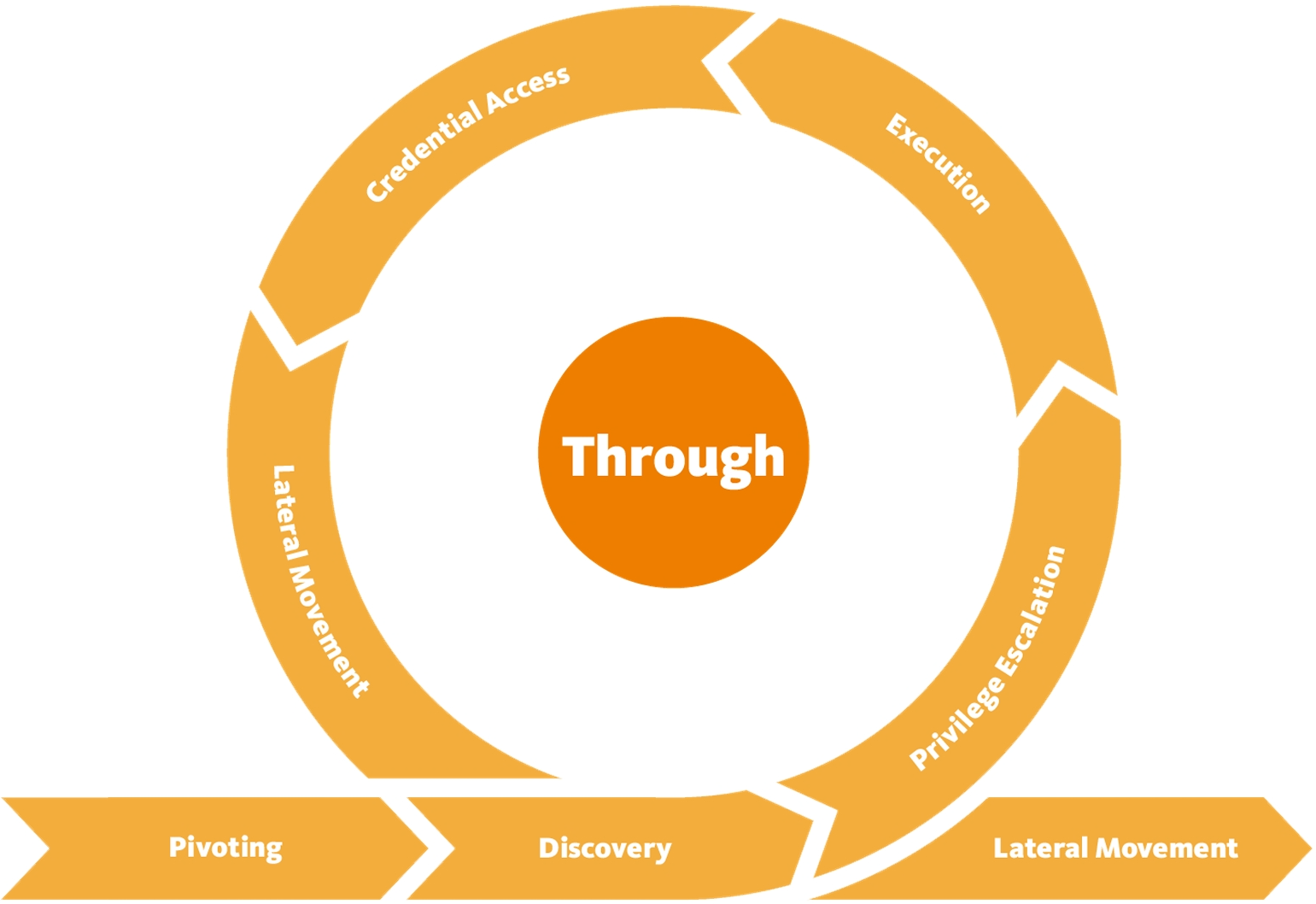
The phases here will be linked to MITRE ATT&CK tactics as examples.
Pivoting
This phase describes the techniques an adversary can use to gain deeper access to the network.
There might not be a direct way to connect to additional hosts on the network. This is where pivoting comes in. Pivoting is where an attacker is able to gain initial access into the network and move onto other systems to gain further access and privileges.
The primary purpose of pivoting is to bypass network segmentation (either physically or virtually) to access networks and systems that are otherwise inaccessible.
This phase can be linked to "Lateral Movement" (TA0008) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0008/
Discovery
This phase describes how an adversary gathers more information about the systems and networks after gaining initial access.
An example will be where an attacker enumerates active user accounts and the privileges granted to them.
This phase can be linked to "Discovery" (TA0007) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0007/
Privilege Escalation
This phase describes how an adversary is able to elevate their privileges to gain more access.
Privilege escalation is where an attacker is able to gain more permissions (i.e., going from a normal user to a admin user). An attacker may use misconfigurations or vulnerabilities found on the system to elevate their access.
Some examples of high privileges are:
- SYSTEM (Windows)
- root (Linux)
- Domain Administrator (AD)/Local Administrator
- User accounts with administrative privileges
- User accounts with specific access or functions
This phase can be linked to "Privilege Escalation" (TA0004) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0004/
Execution
This phase describes the techniques used by an adversary to run malicious code locally or on remote systems.
An attacker can attempt to run malicious code such as C2 scripts, trojans, scheduled tasks, and more by pairing with different techniques.
This phase can be linked to "Execution" (TA0002) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0002/
Credential Access
This phase describes the techniques used by an adversary to steal credentials such as account name and passwords.
An attacker can use techniques such as setting up a keylogger to obtain the credentials for users using the compromised system.
This makes detection harder as the attacker is using legitimate credentials. Credentials stolen can also be used to elevate permissions (e.g., dumping the admin credentials).
This phase can be linked to "Credential Access" (TA0006) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0006/
Lateral Movement
This phase describes the techniques used by an adversary to gain access and control remote systems on a network.
Lateral movement allows an attacker to gain access to more systems in order to achieve their primary objective.
An example will be where an attacker is able to use the user credentials obtained from the previous stage to login to different systems without getting detected to achieve their objectives.
This phase can be linked to "Lateral Movement" (TA0008) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0008/
Phase: Out - Action on Objectives
This series of phases focuses on fulfilling the adversary's objectives after gaining sufficient access and privileges to the target network.
The following phases are: 15. Collection 16. Exfiltration 17. Impact 18. Objectives
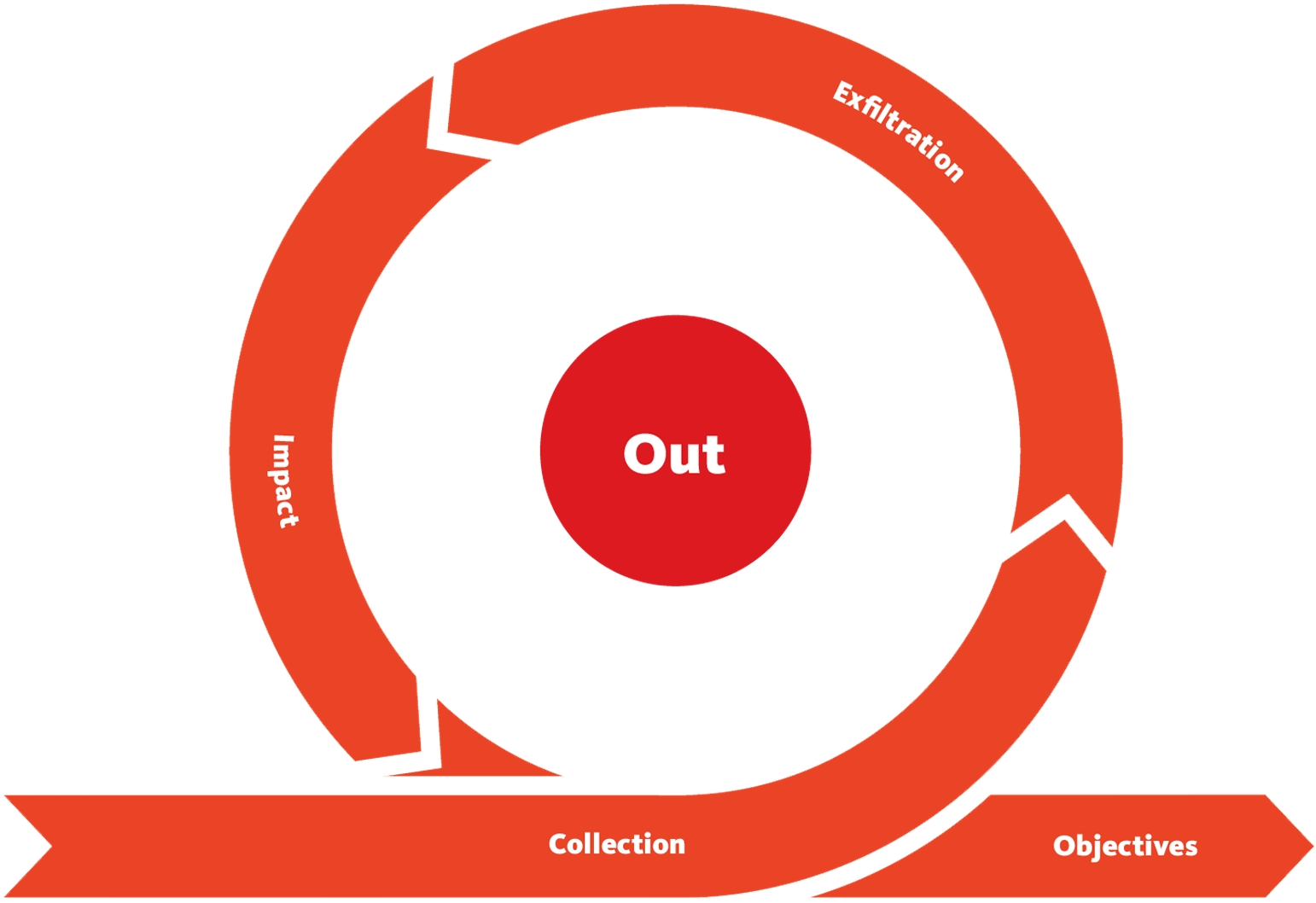
The phases here will be linked to MITRE ATT&CK tactics as examples.
Collection
This phase describes how an adversary will gather the information and data of interested to be exfiltrated.
After hunting for the assets of interests, an adversary can compromise the Confidentiality, Integrity, and Availability (CIA) of the target.
This phase can be linked to "Collection" (TA0009) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0009/
Exfiltration
This phase describes the techniques used by an adversary steals data from the target network after collecting it.
An attacker can use different ways to move the data out of the target network after collection such as packaging and encrypting it to avoid detection. A C2 server is usually used to transfer the data out of the network.
This phase can be linked to "Exfiltration" (TA0010) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0010/
Impact
This phase describes the techniques used by an adversary to disrupt the integrity and availability of the target.
An attacker's goal can be to compromise the availability of the target systems by performing actions such as deleting or tampering with critical data, wiping disks, and more or attacks such as a Denial of Service (DoS) attack.
This phase can be linked to "Impact" (TA0040) in the MITRE ATT&CK framework:
https://attack.mitre.org/tactics/TA0040/
Objectives
This phase describes the adversary objectives. Depending on the motivation and goals, attackers can run ransomware on the target systems for financial gains or release confidential documents to damage reputation.
Diamond Model of Intrusion Analysis
The Diamond Model of Intrusion Analysis is composed of 4 core features:
- Adversary
- Infrastructure
- Capability
- Victim
The Diamond Model also has 6 meta features:
- Timestamp
- Phase
- Result
- Direction
- Methodology
- Resources
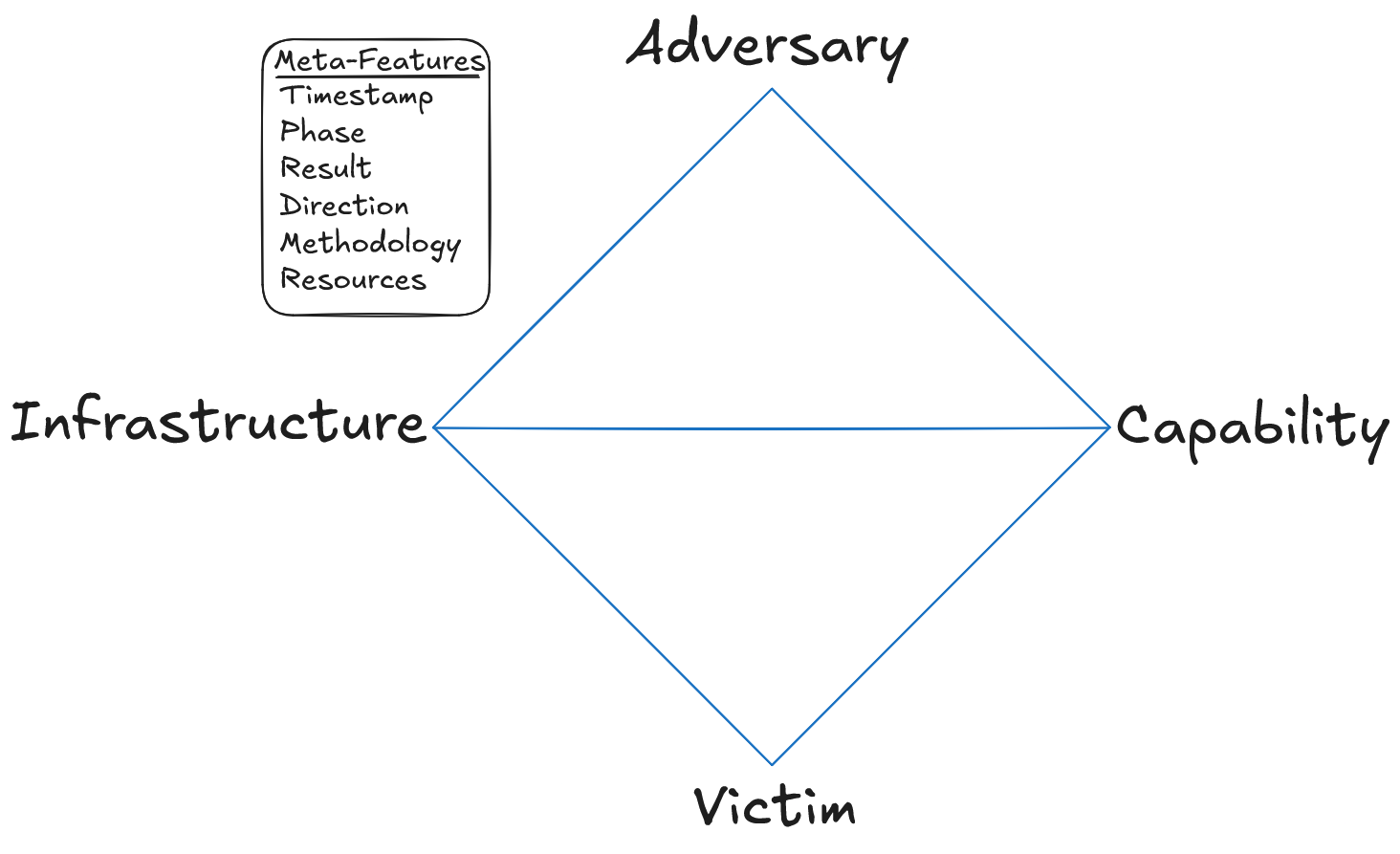
The Diamond Model establishes the fundamental atomic element of any intrusion activity. It carries the essential concepts of intrusion analysis and adversary operations while allowing the flexibility to expand and encompass new ideas and concepts.
Adversary
An adversary is also known as the attacker, cyber threat actor, hacker, and enemy. The adversary or adversaries are the people behind the cyber attack.
In the Diamond Model, an adversary is an actor or organisation responsible for utilising a capability against the victim to achieve their intent.
It is important to know the distinction between adversary operator and adversary customer as this will help us understand the intent, attribution, adaptability, and persistence by helping to frame the relationship between an adversary and victim pair.
| Name | Description |
|---|---|
| Adversary Operator | The operator is the person(s) conducting the intrusion activity. |
| Adversary Customer | The customer is the entity that stands to benefit from the activities conducted during the intrusion. It can be the same person as the operator or a separate person or group. |
An example will be where an adversary customer could control different operators simultaneously where each operator can have their own capabilities and infrastructure.
Victim
The victim is the target of an adversary. A victim can be an organisation, individual, IP address, domain, etc. It is essential to understand the difference between the victim persona and assets as they serve different analytic functions.
| Name | Description |
|---|---|
| Victim Personae | This is the people and organisations that are being targeted and whose assets are being attacked and exploited. |
| Victim Assets | These are the attack surface and can include items such as systems, email addresses, hosts, IP addresses, online accounts, etc. These items are where the adversary will direct their capabilities. |
A victim can be an opportunity for the adversary to gain initial access or foothold on the organisation they are targeting. For every cyber attack, there is always a victim.
Capability
The capability is also known as the tools, skills, and techniques that the adversary will use. The capability highlights the adversary's tactics, techniques, and procedures (TTPs).
Capabilities can include less sophisticated methods such as manual password guessing to more sophisticated techniques such as developing custom malware or tools.
The capability capacity are all of the vulnerabilities and exposures that the individual capability can use.
An adversary arsenal is a set of capabilities that belongs to an adversary. The combined capacities of the adversary capabilities forms the arsenal.
Some examples of capabilities are skills to develop malware, acquiring malware, or services.
Infrastructure
The infrastructure is the hardware or software that the adversary uses to deliver a capability or maintain control of capabilities. Infrastructure can be items such as domains, email addresses, IP addresses, USB devices, and more.
An example will be a Command and Control (C2) server that is used to exfiltrate data.
There are 2 infrastructure types:
| Infrastructure Type | Description |
|---|---|
| Type 1 Infrastructure | This type of infrastructure is controlled or owned by the adversary. |
| Type 2 Infrastructure | This type of infrastructure is controlled by an intermediary. The intermediary might not necessarily be aware of it. This usually has the purpose of obfuscating the source and attribution of the activity. This can be compromised email accounts, domain names, servers, etc. |
Service Providers are organisations that provide the services considered critical for the adversary availability of Type 1 and 2 infrastructure. These organisations are usually not malicious and are just providing a service. Some examples are Internet Service Provider (ISP), domain registrar, webmail providers, cloud hosting, etc.
Event Meta-Features
There are 6 possible meta-features that can be added to the Diamond Model. Meta-features are not required, but can add some valuable information or intelligence to the model.
| Meta-Feature | Description |
|---|---|
| Timestamp | The timestamp is the date and time of the event. There are different formats on how the date and time can be recorded such as 2025-01-21-14:11:53.112. This can help determine the adversary's patterns and activities. |
| Phase | These are the phases of an attack. Malicious activities do not occur as single events, but rather as a sequence of events. Some examples that can be used are the Cyber Kill Chain or the Unified Kill Chain. |
| Result | This feature captures the results and post-conditions of an adversary's operation. The event results can be labelled as "success", "failure", or "unknown". Other approaches can be linking it to the CIA triad such as confidentiality compromised, etc. |
| Direction | This feature describes the host and network based events and represents the direction of the intrusion attack. The Diamond Model defines 7 potential values for this: Victim-to-Infrastructure, Infrastructure-to-Victim, Infrastructure-to-Infrastructure, Adversary-to-Infrastructure, Infrastructure-to-Adversary, Bidirectional or Unknown. |
| Methodology | This feature will allow an analyst to describe the general classification of the intrusion (e.g., phishing, DDoS, port scan, etc.). |
| Resources | According to the Diamond Model, every intrusion event needs one or more external resources to be satisfied to succeed. Some examples of such resources can be software, hardware, knowledge, facilities, access, funds, information, etc. |
MITRE
MITRE Corporation was established to advance national security in the US. MITRE has created several cybersecurity frameworks:
- ATT&CK (Adversarial, Tactics, Techniques, and Common Knowledge) Framework
- CAR (Cyber Analytics Repository) Knowledge Base
- ENGAGE
- D3FEND (Detection, Denial, and Disruption Framework Empowering Network Defence)
- AEP (ATT&CK Emulation Plans)
The different frameworks allows defenders to understand the TTPs of adversaries and form plans to detect and respond to intrusion attempts.